Adding ConfigServer Firewall Blocks To Cloudflare
Why Adding ConfigServer Firewall Blocks To Cloudflare
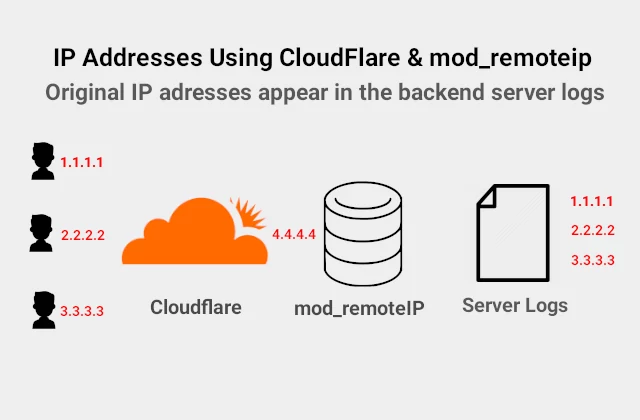
Ideally after installing mod_cloudflare on Apache, we should be able to get the real IP of the visitors. This is true for any application that is in operation after Apache. Unfortunately, the firewall runs before mod_cloudflare comes into effect. This means csf doesn’t see the correct remote IP address for requests via CloudFlare. It sees is as a part of Cloudflare IP block.
As a consequence, the IP cannot be blocked because the firewall is seeing the whitelisted CloudFlare IP addresses.
BLOCK_REPORT = “” Option in /etc/csf/csf.conf
BLOCK_REPORT = “” option in /etc/csf/csf.conf gives you a workaround this problem. Here you can add a script name that is run whenever LFD (Login Failure Daemon) adds a new IP to the firewall deny list.
On the other hand CloudFlare has a simple API which can be used to add IP address blocks. Here you can find a simple script , utilizing Cloudflare’s API, that you can manually add to your server installation and i.ts path to /etc/csf/csf.conf
Alternatively there is an script on Github which installs the script and adds the line in /etc/csf/csf.conf. During the installation you will be prompted to enter your Cloudflare account API and email address.